A few weeks ago I was tasked with performing a mobile application test on iOS. I've tinkered with Android a few times in the past, going so far as to actually create malicious applications for a POC project however I hadn't really looked at iOS or even the general methodology around mobile application testing, so in this post, (which I hope to make into a multi-part series) I'm going to attempt to walk you through some of pre-requisites for testing and show a couple of quick wins to get you started.
First off, we need to understand the mobile testing landscape so we know where to start. Lets take a look at a quick diagram that I drew up with Xmind. I often find that a diagram is more helpful as it allows me to visualize the core concepts around a technology or create a methodology that works for me whilst also assisting in breaking down unfamiliar topics so that we don't end up getting overwhelmed during learning.

So starting at the top, we have the most recent version of OWASP's Top 10 (2024) for mobile. See link below:
The OWASP Mobile Top 10 is a list of the most critical security risks facing mobile applications and provides guidance for developers, testers, and organizations to understand and address common security challenges in mobile app development. If you have ever done any web application testing then you will be familiar with format and how it works. We can use this list almost as a quick checklist of issues to look for in the mobile application however it doesn't actually provide us with the methods, for this we need the MASTG. MASTG stands for "Mobile Application Security Testing Guide" and is a comprehensive manual for mobile app security testing and reverse engineering. See link below:

Before we get ahead of ourselves, lets quickly talk about the 2nd item in the Xmind diagram, OWASP's MASVS. MASVS stands for "Mobile Application Security Verification Standard" and it is a set of security standards for mobile apps that provides guidelines for developing, testing, and securing mobile applications. Mobile app developers can and should use MASVS as a guide to assess and improve the security posture of their mobile applications. By following the recommendations outlined in MASVS, developers can enhance the resilience of their apps against common security threats and vulnerabilities. See link below:

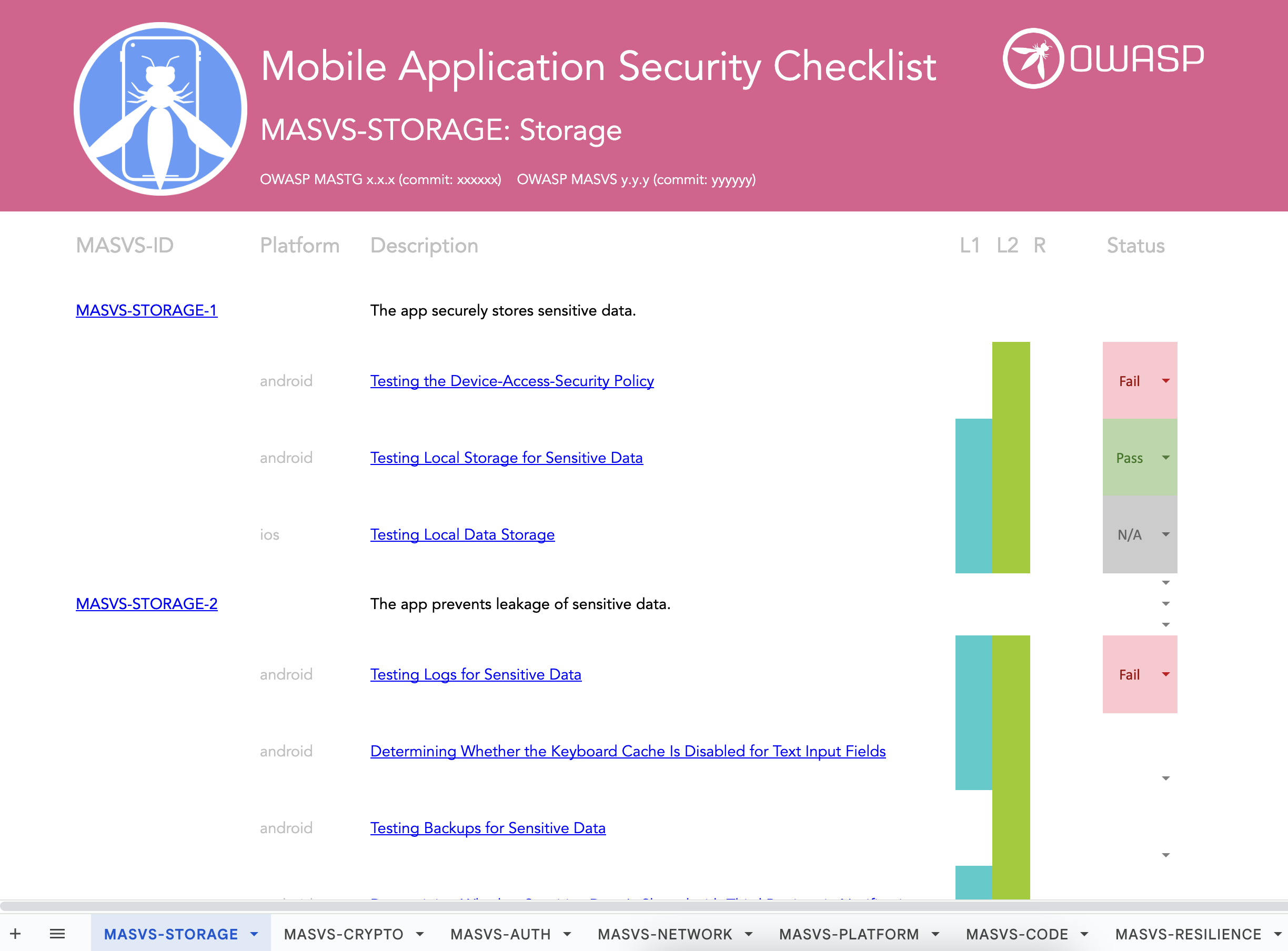
We can actually leverage MASVS alongside the MASTG to ensure that we provide full testing coverage of the application, regardless whether its an Android or iOS application we are testing. The standard is divided into various groups of controls, labeled MASVS-XXXXX, that represent the most critical areas of the mobile attack surface ( Storage, Crypto, Auth, Network, Platform, Code, Resilience and Privacy) and a description of the test required which actually links back to the MASTG testing guide which contains the specific methodology for whichever OS your testing. See image below:

See link below to download a copy of the MAS Checklist:
Ok, so finally we come to last item in the mindmap - something that I call "Crossover Techniques". This is a term that I've coined, it covers the testing techniques and setup upon which most mobile application tutorials seem to be based around these days, which is intercepting and capturing traffic via Burpsuite. In my opinion this only really covers a small portion of mobile application testing, for sure its definitely a part of mobile testing as most applications will be sending and receiving data to a backend server and/or communicating with an API, however we really need to dive into the guts of the application to give it full coverage, and thats where MASTG and MASVS can assist us.
Before we even get to testing the application there is typically a bit of setup required on either a physical device or emulator. As I quickly learned during my iOS testing, if the mobile application isn't working as expected, there are a number of things that might need tweaked, for example bypassing SSL/TLS. Some applications will implement SSL Pinning, which prevents the application from accepting your intercepting certificate as a valid certificate. This means that you will not be able to monitor the traffic between the application and the server. Another example is the having to circumvent applications that detect they are running on a ROOTED device or are running in an emulator.
So where does that put us in terms of what we need to do and what techniques are required? Well it depends on what OS we are performing the mobile application test on. For iOS, testing really needs to be done on an actual physical device, whereas on Android we test on both, physical and emulator. If we refer back to the Xmind diagram, you will see that I've now updated the Crossover Techniques to include some of things that we need to consider and will need to setup as we progress:

Wrapping things up for this post, I recommend you go and take a look at the resources that OWASP provides using the links above. For future posts, I will attempt to provide a high level overview of setting up a working environment and device for iOS testing.

