Server Side Request Forgery (SSRF) is a vulnerability that describes the behaviour of a server making a request that is under the attackers control. When using a SSRF attack, an attacker can abuse the functionality on the server to read or update internal resources. Typically, SSRF attacks are a result of the target application having the functionality for importing data from a URL or publishing data to a URL which we can tamper with. By modifying the calls to this functionality, we can manipulate the request that goes to the server, whereby the server tries to read the manipulated URL allowing the attacker to read data files or connect to internal services which are not intended to be exposed to external users.
In the following examples, I will demonstrate how we can read the password file from our server as well as how we can get the server to make external requests to another website.
Example 1
In this example, SSRF is present within the image URL field when creating a new message. We begin by adding a new message, I have added the text, ‘ssrf4’ into the Subject and Text field, as well as ‘sometext’ into the Image URL field – it is this string that we will modify in our request via Burpsuite.
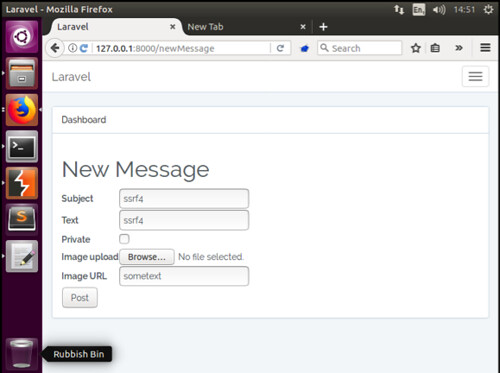
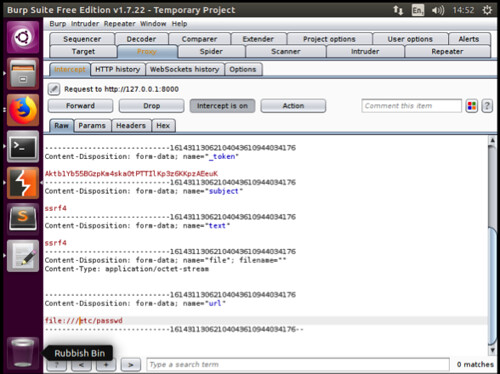
We click the post button to create our new message and immediately capture the request in Burpsuite. Next we replace our original ‘sometext’ value with the following syntax: file///etc/passwd, as shown below:
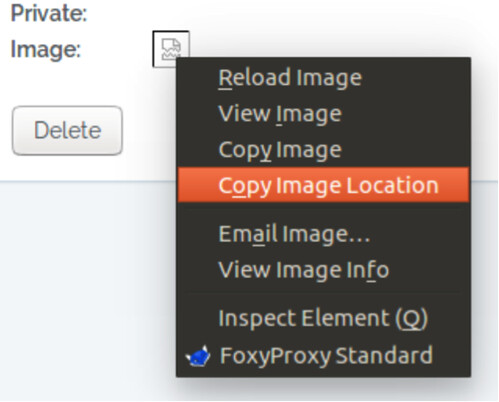
We then forward the request to the application. Returning to the web browser, you will see that the application has accepted our change and the newly created message is shown. Clicking upon message title we will be shown the message in full (Be sure to turn off intercept in Burpsuite prior to trying to view the message). At this point, we note that everything looks normal, however if we right click on the icon where we would expect the image to appear, we can select copy image location, as shown below:
Copying and pasting the image location into a new browser window, will result in the browser presenting us with a prompt to save a binary file, as shown below:
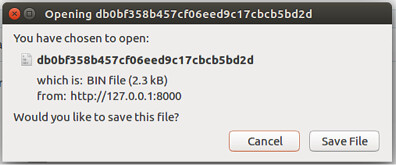
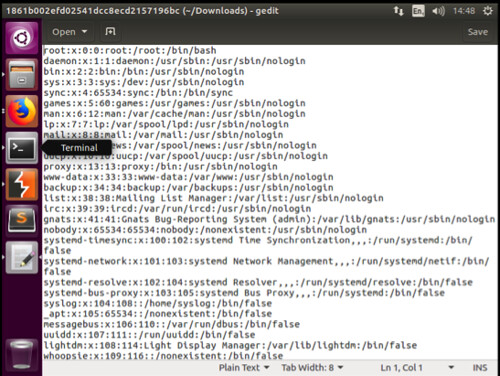
Subsequently, saving and opening this file we see that the contents of the Linux passwd file has been returned to us, as shown below:
Example 2
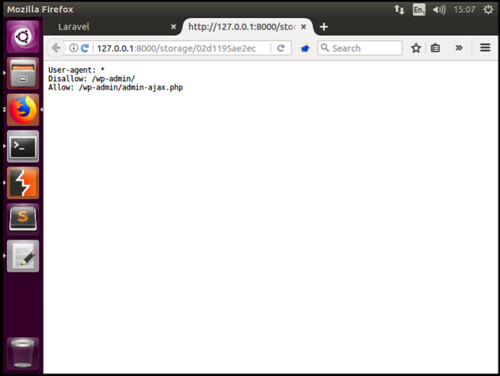
In our second example, we will use SSRF to perform a Remote File Inclusion(RFI). RFI is the process of including remote files through the exploitation of input that not properly sanitized, allowing the contents of the external URL to be injected. Our example, isn’t particularly dangerous as we will simply be using it to read the robots.txt file contained on the Secarma.co.uk website, however using the same techniques, a hacker could host their own website containing malicious PHP scripts. If they were able to identify that SSRF was present within an application, they could submit a malicious link which our server would then attempt to read and execute.
Again, we follow the same procedure as above, we create a new message, complete the subject, text and image url fields and intercept the request in Burpsuite, this time we ask the request to fetch an external resource as shown below.
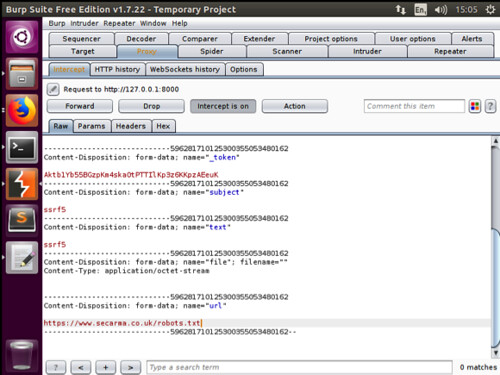
Once we change and forward the request, we return to the application and copy the image location into a new browser tab. The result, the contents of the robots.txt file is presented back to us, thus meaning that we were able to get the application server to request both internal and external files on our behalf..