Thought I would do a quick write up of a small bug that I found late last year (2018). Unfortunately, the bug was considered out of scope as it was classed as 'self XSS' therefore it wasn't eligible for any reward, however I was still happy with the result of finding something as this was my first proper attempt at doing a Bug Bounty on the Hackerone platform.
Choosing a target:
Being a beginner in Bug Bounty hunting, I chose a target that had a large scope. I gravitated to Grab as its scope was designated as *grab.com. I felt I needed some practise on subdomain enumeration, so this was the ideal opportunity to look at using one of the many tools available, for this task I used sublist3r.
Within my results I noted the subdomain of driver.grab.com, so I decided to look into this further.
Google Dork
At this point I decided to see if there was any endpoints or references to this subdomain on Google. Using the simple google dork site:driver.grab.com, I noted that there was two pages of results. I began quickly scanning to see if there was anything that caught my attention, on the 2nd page of results this one caught my eye:

Visiting the URL, I discovered a driver registration form, as shown below:

The "Full Name" field had no input sanitization and allowed the inclusion of the typical characters that should be removed < > ' ". There was however a restriction on the "Handphone" and "IC Number" fields, as they would not allow me to add a random string of numbers such as 00112233445566. They actually required valid numbers.
After some trial and error and a lot of googling I found two numbers that were accepted. Finally I submitted the form and was immediately greeted with my XSS payload, as shown below:
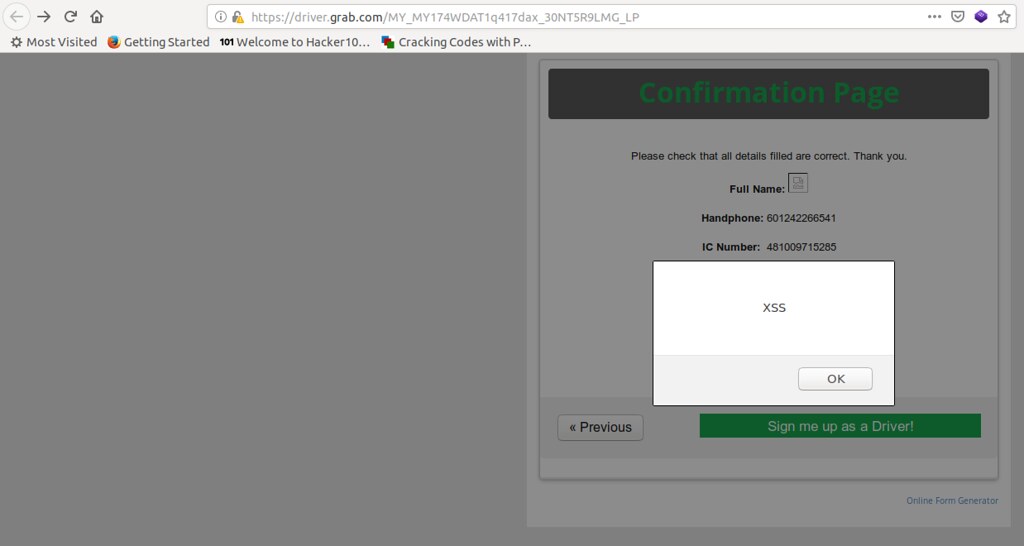
Feeling super pumped by the whole experience, I filed a report and sent it away to Hackerone, however I had missed the note that excluded self XSS and therefore I was ineligible to receive a reward, as per the response from Hackerone below:

Final Thoughts:
Remember, its not all about the money, sometimes the greatest reward is the journey and achievement of learning something new.
Thanks for reading.
(Note: The URL shown in the images is no longer available and has been taken offline since I reported it)
