Over the weekend I participated in @zseanos live stream bug bounty mentoring session in which he created an application for viewers to hack live and submit reports and bugs in realtime. He then walked through some of the bugs and the methodology used to find them. I found this technique for searching for XSS particularly interesting, so thought I would share it.
Furthermore, Sean has left the application online to practise on, so be sure to try this technique and some of the others out over at:
bugbountytraining.com/FFH/
The recorded session is also online over on Sean's YouTube channel: YouTube
Starting Point
So I kinda jumped the gun when I starting poking around this application and missed some things that I would usually check - in particular I missed the XSS on the homepage, furthermore I've never actually seen this technique before.
View page source: ctrl+u(Chrome) or right click view page source.
Start by looking for JavaScript variables that are blank. To do this use the search facility: ctrl+f to search for JavaScript variables. Keywords to search for include: var = "" = ''
Result from searching for var
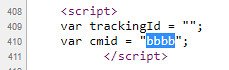
Two variables are shown without any parameters trackingId and cmid.

Begin by trying to inject a parameter value into these variables: https://www.bugbountytraining.com/FFH/?trackingId=trackingId
Returning to viewsource, we note that trackingId=trackingId remains blank, nothing was returned.

So next we try to inject into the cmid variable: https://www.bugbountytraining.com/FFH/?trackingId=trackingId&cmid=cmid
This time when we return to viewsource, we see that it was possible to inject into the cmid variable, as shown below:
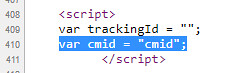
Next step is check if we can include the characters typically used in XSS injection: <"'> As per the screenshot below, it is possible to include these characters so we can try an xss payload.

Final Payload
https://www.bugbountytraining.com/FFH/?trackingId=trackingId&cmid=cmid"-alert(0)-"
Screenshot below shows the reflected XSS popping:

Next Step: Investigate why trackingId didn't do anything.
Try different variants of the variable name, so for example try replacing trackingId with different variations, maybe the developer used a shortened version, so instead of trackingId maybe they used id, for this example its actually tid that works: https://www.bugbountytraining.com/FFH/?tid=tid&cmid=cmid

Using this information, we can repeat the steps above to test for injection characters or just try the same XSS payload on both the variables:
https://www.bugbountytraining.com/FFH/?tid=tid"-alert(1)-"&cmid=cmid"-alert(2)-"
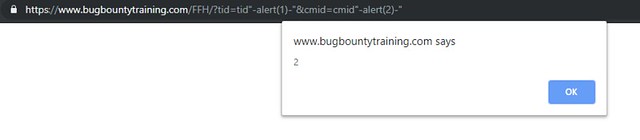
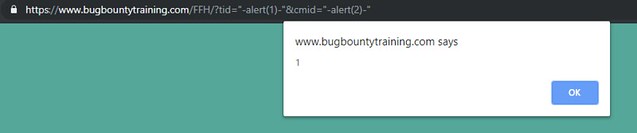
Confirmation of the injection using viewsource:
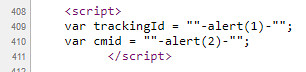
Be sure to check out Seans video as there is also a third variable which can be manipulated which goes unnoticed unless you change the User Agent. Top tip considering many applications are developed with mobiles/tablets in mind.
Quick note:
In Zseano's example, he used a parameter name which was the same as the variable name: trackingId=trackingId cmid=cmid
However, you could also try using your own unique parameter strings, for example: https://www.bugbountytraining.com/FFH/?trackingId=aaaa&cmid=bbbb